We all get hundreds, maybe even thousands, of phishing emails over the course of the year. Lurking in our inboxes, these emails carry risks that would spook any sys admin. In recent years, the tools to combat these annoyances have increased in their effectiveness in catching and preventing these emails. In combination with better tools, awareness among engineers and end users has increased, though it has a long way to go before we have perfect protection.
Unfortunately, this also means is that threat actors are developing more advanced techniques and investing more energy into their attacks to get unsuspecting or inattentive end-users hooked. Some phishing attacks are starting the blur the lines between traditional phishing and full-blown social engineering.
On a dark and spooky night (just kidding it was a Friday afternoon) one of our clients received what may look like a typical phishing email designed to appear as though it was from the company CEO (personal data redacted):
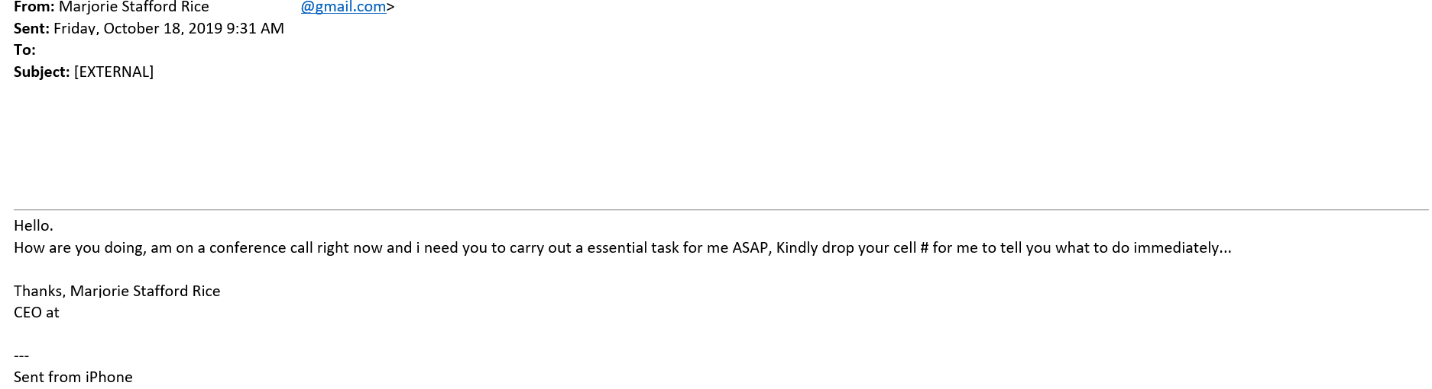
This email is deceptively simple. It doesn’t have the typical company email signature, but using “Sent from my iPhone” may make the email more believable. The message is simple, and again, believable, as the end user might typically be asked to complete tasks for the CEO while she is on conference calls.
A suspicious user might notice it’s from a Gmail account. What made this event different is that the attacker also created a LinkedIn account and attached that email address, in essence attempting to impersonate the CEO.
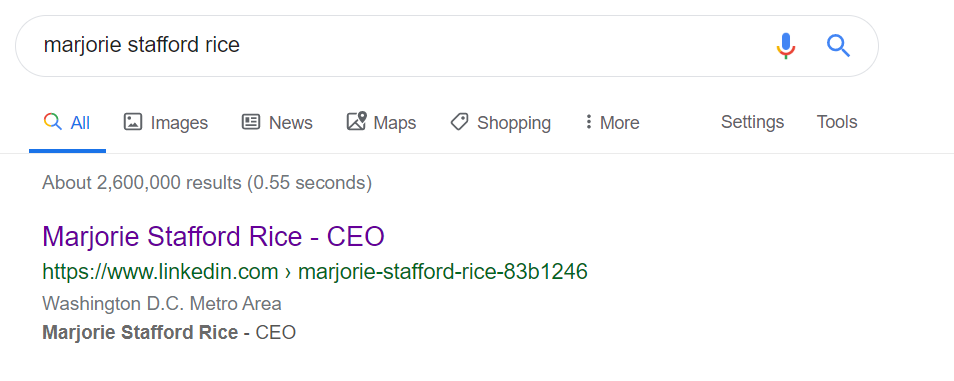
Although this was just one additional small step in this attack, the threat actor may have been able to instill a sense of urgency with the target victim, enough to get a new employee or someone just at the right moment to fall for this trick with little effort needed from the attacker. With the added effort of making a fake LinkedIn account, the reputation of this false identity can easily be increased to further legitimatize the attack, even if the employee makes a cursory Google of the suspicious email address.
To combat these attacks there are both technical controls and further security awareness efforts enterprises need to take to reduce the impact and chances of becoming victims to phishing and social engineering attacks. Technical controls that combat this are impersonation filtering tools and phishing detecting via secure email gateways. Ultimately, items will still get through and the focus should be strong security awareness trainings that promote users to be ever vigilant against these types of attacks.
Our cybersecurity team takes an integrated approach to assessing your risks as they apply to people, processes and technology. If phishing attacks and email security are a top concern for your company contact us today!